Path: Design
Technology: Network Security
Area: Access and Identity Management
Vendor: Cisco
Software: 1.X, 2.X
Platform: ISE Physical Appliance, ISE Virtual Appliance
Cisco Identity Services Engine is a Network Access Control solution that helps to concentrate all enterprise network identity policies in one place. ISE is a point of the network where all network access methods and identities are verified against defined ruleset and authentication sources. Based on configured rules ISE is able to provide granular access rights to services based on many factors and contexts like AD group membership, the physical location of the user, device type, OS version, time of day, and more. The fundamental principle for ISE is to act as a Radius server. Anyway despite the Radius is the primary communication protocol between ISE and network devices, there are a bunch of refinements to legacy solutions like Radius Change of Authorization flows, OS and devices profiling, posture assessment procedures for security compliance alignment, 3rd party devices onboarding, or guest portal redirection methods.

Cisco ISE Deployment models
Implementing Cisco ISE you should be aware of the deployment modes and architectural functionality available from Cisco. Choosing the deployment option, it is worth to mention possibilities. In general, you have two options:
- Deployment options
- Standalone Deployment (built on one ISE node)
- Distributed Deployment (built with more than one ISE nodes)
Example of Small distributed deployment.
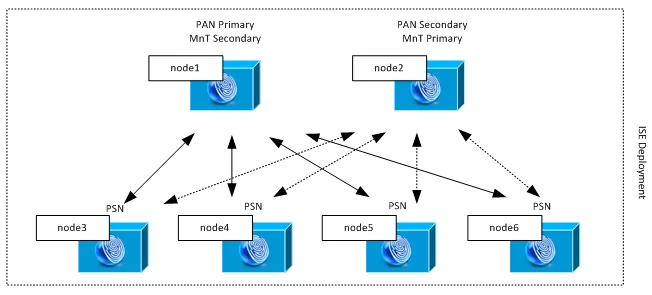
Example of medium-scale distributed deployment.
Which one to choose?
Depending on your organization requirements, scale, number of users and sites you need to choose one of available deployments. There is no strict requirement and we saw many quite large designs based on small deployment type. One node deployment (aka standalone) is suitable for PoC projects or lab / testing environments where no high availability is required. To better understand the deployment modes it is wise to get familiar with the ISE nomenclature.
ISE Architecture and nomenclature:
- Node – Individual instance – Physical Appliance or Virtual Appliance
- Persona/Node Type – This one is often used interchangeable and determines the service provided by particular node:
- Administration (PAN) – Administration Node is a single point of ISE deployment configuration. This persona provides full access to administration GUI
- Policy Service (PSN) – Policy Service Node is a node that handles traffic between network devices and ISE (its IP is used as Radius for devices). To achieve radius traffic sharing you can scale the PSNs up.
- Monitoring (MnT) – monitoring node is responsible for logs aggregation across deployment.
- Role – Applies to Administration and Monitoring nodes.
- Standalone – related to standalone deployment – node is not aware of each other and acts alone.
- Primary – role in distributed deployment where for example administration persona is the primary for all configuration tasks.
- Secondary – role in distributed deployment where for example administration persona is secondary for configuration tasks. Secondary GUI is available for configuration only when:
- Primary fails and there is PAN Failover configured
- Secondary is manually promoted to Primary
Example of mid-sized distribution deployment. PSN nodes act as a radius servers for network devices and there are four of them. Administration Persona is active on two nodes. Node 1 takes role of Primary Administration Node and Node 2 takes role of Secondary Administration Node. All configuration and maintenance tasks are done in Primary Administration Node and settings are propagated across whole deployment in the same time. The MnT role is reverted for load sharing purposes. All events on PSN personas are relied to MnT primary and secondary nodes.

We’ve compared popular Network Access Control solutions to make it easier for you to choose (or test) the system suitable for your organization.

Author: Marcin Bialy






