What is Cisco ASA FirePOWER?
The flagship firewall of Cisco – the Cisco ASA (Adaptive Security Appliance) and FirePOWER technology (the result acquisition of Source Fire company by Cisco in 2013) lied down the foundation of the “next-generation firewall” line of products in Cisco’s portfolio: ASA FirePOWER Services. This next-generation firewall is composed of widely known ASA-OS and software module (SFR) that takes care of main “next-generation” functions like Application Control, Intrusion Protection, Anti-Malware, and URL Filtering.
ASA FirePOWER licensing
Align with next-generation functions there is appropriate licensing proposed by Cisco, in fact, similar to other vendors, where licensing goes according to firewall functionality (you can read more about other vendors licensing here). In ASA FirePOWER there are the following licenses available:
- Control License – allows user and application control by adding application and user conditions to access control rules. To enable control you need to enable protection as well. Doesn’t expire.
- Protection License – includes intrusion detection and prevention behavior, file control, and Security Intelligence filtering. Doesn’t expire.
- Advanced Malware Protection (AMP) license – performs malware code detections and blocking when transmitted over the network. The license is time-based.
- URL Filtering License – used in access control rules that determine the traffic that can traverse the network based on URLs and web categories requested by monitored hosts. Categories are correlated with information about those websites, which is obtained from the Cisco cloud by the ASA FirePOWER module. The license is time-based.
Besides the licenses described above ASA OS itself is also licensed as it was before. It means
- Security Plus license for small platforms (5506X, 5508X, 5512X) enables:
- More VLANs
- Active-Standby Clustering
- Higher performance
- Low-End platforms don’t support contexts
- VPN – Anyconnect licensing
- Plus
- basic VPN client connectivity
- Third-party IPsec IKEv2 RA clients
- Per Application VPN
- Cloud Web Security and WSA
- NAM module (802.1x)
- AMP for endpoints enables (AMP itself licensed separately)
- Apex
- All above
- Network Visibility Module (from 4.2)
- Posture (Compliance and remediation with ISE, Apex for ISE needed)
- Suite B or NG Encryption
- Clientless VPN
- ASA multi-context mode remote access
Firepower Management Center (FMC) and network architecture
In red, you can see the production traffic flow. Traffic flows normally from appliance to appliance between regular ASA interfaces based on a routing table (or PBR). However, ASA internal traffic redirection which is done by Modular Policy Framework (MPF) is responsible for directing the production traffic to FirePOWER modules (know also as SFR module) which is optional by design but of course essential for next-generation firewall functions to take effect.
This traffic redirection is performed within the internal ASA interface connecting the ASA data plane and SFR module plane. Traffic that is directed to the SFR module is inspected under different conditions and actions are made according to configured policies. Those policies called Access Control Policies are in turn configured from a management station called Firepower Management Center (FMC) where all the modules are synchronized to. FMC can be VM as well as a physical appliance. Black lines depict Firepower management traffic from FMC to sensors and from sensors to FMC. This black line is typically some kind of management segment within the network. Designing for FirePOWER in your network you need to remember that sensors use the mgmt segment for logging to FMC and FMC uses mgmt to monitor sensors, pull data, and push configuration. That means that this part of the network could be somehow utilized especially by logging traffic.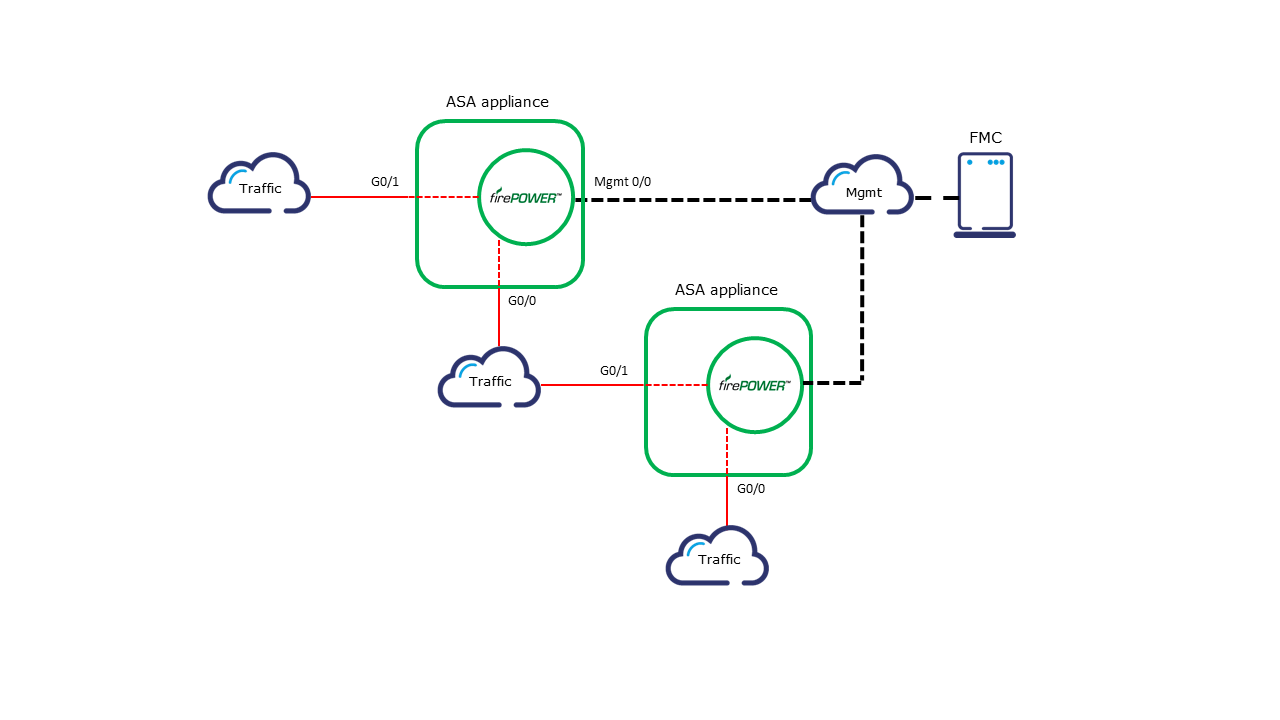
More in Cisco Firepower Online Training
Let us guide you through Cisco Firepower Threat Defense technology (FTD) along with Firepower Management Center (FMC) as security management and reporting environment.
Author: Marcin Bialy

