I would like to share my experience with VPN Remote Access and Multi Factor Authentication with products from Cisco and Duo Security:
- Cisco Identity Services Engine 2.X,
- Cisco ASA 5500-X
- Anyconnect Secure Mobility Client (VPN client)
- MFA Cloud based services from Duo Security
Background of Multi Factor Authentication
Multi Factor Authentication (MFA) is already quite well known approach in achieving more secure authentication process. The aim of this type of authentication is to provide additional level of security ensuring that authenticating user proves his identity with different factors, independent from each other. The MFA paradigm is that the user proves his identity by providing information that he knows (example: user credentials) and then providing information based on what he owns (example: hardware or software token). This procedure increases the probability of genuine authentication and make sure it is not fake. In a hypothetical scenario an attacker can steal user credentials by spying, sniffing or guessing if password is not secure enough, but when using MFA the use of another factor makes such attack more difficult because the attacker does not possesses the second factor for authentication. The second (or third) factor can be of different kinds for instance physical, application based, connected or standalone. They could be a physical or logical tokens, phone calls, text messages or push messages.
How does second factor authentication work?
Lets quickly introduce popular types of different authentication factors.
Credentials
The most popular – users knows their username and passwords and provide them while authenticating.
Certificates
Also a popular factor – users have enrolled with their personal certificates and uses X509 framework to authenticate. If you want to know about the certificate authentication process in detail have a look at ITU standards here.
Tokens
Token provides one-time password that changes in fixed time intervals, for example every 60 seconds. One-time password (OTP) is displayed with synchronization with reference server often known as token server. Synchronization is done between token internal clock and token server clock. Both parties generate pseudo random number thanks to OATH algorithm or any variation of OTP generation algorithm. Tokens can be hardware (i.e. RSA SecureID hardware) or software based (i.e. mobile apps for iOS or Android). The downside of the hw tokens is that they are expensive in implementation.

RSA SecurID hardware token example

Cerb Software token MFA example
Push notifications
Good choice for big implementations (often cheaper than hardware tokens) is push notification method where User is prompted actively by mobile App to Approve or Decline the fact of authentication. This method is used in conjunction with smartphone device and installed mobile app on it. This kind of authentication factor is used in our case study.

Duo MFA Push Notify factor example
SMS Passcodes
Another type of factor is sending SMS code which needs to be provided by user during authentication prompt. This requires SMS gateway for that process.
Callback phone
Some of market solutions enable “callback phone’ that is automaticaly processed after first factor is correctly passed. After phone call, user is able to press required key. This method works well for offline users for example those who do not use the smartphones.
The project aim and chosen solution
The aim was to increase a security level for User VPN authentications. Customer had Cisco infrastructure with high level of integration. After business needs analysis and infra assessment and then several days of Proof of Concept project the choice was Duo Security product for MFA solution because of its flexibility and user friendly interface. There were also signs that it will smoothly integrate within the Cisco architecture components.
Architecture components and authentication flow
The steps of authentication is as follows:
- User connects with Anyconnect Secure Mobility Client to ASA Headend
- User is prompted to provide Domain credentials
- Credentials are sent to VPN Headend encrypted
- ASA VPN checks credentials with Duo AuthProxy then Duo with ISE. Both communication via Radius.
- Cisco ISE in turn verifies user and password with AD Controller
- AD responds to ISE. If fails ISE sends the Radius Reject packet back to Duo and then Duo to ASA
- If succeeded Duo sends the request with username to Duo Cloud
- Duo Cloud then pushes the Approve / Deny message to Mobile App of authenticating user
- User accepts (or denies) the connection. If denies, the Radius Access Reject is send via Duo AuthProxy to ASA and connection is torn down.
- After Accept from Mobile information is going back to Cloud and then to AuthProxy and finally is landing on ASA VPN Headend
- ASA establishes VPN connection with Anyconnect
- Last but not least, the accounting message that confirms the established session is sent from ASA to ISE for logging and accounting purposes (piggybacking IP address, Username, Timestamp and more)
Traffic flow high level view – MFA authentication
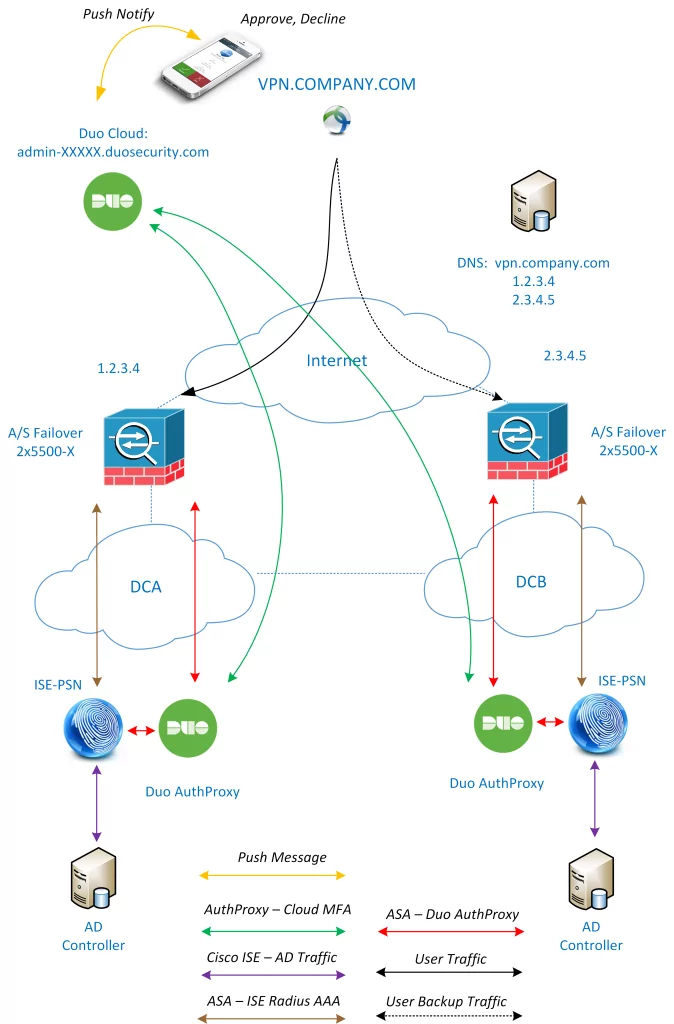
VPN Multi Factor Authentication idea traffic flow
ASA VPN Headend
The ASA configuration part is very similar to regular remote access implementation with Cisco Anyconnect. One thing to mention is accounting and authentication server part. In our case study ASA acts as a radius client to Duo Authentication Proxy and in parallel to ISE Policy Service Nodes. The Duo Authentication Proxy in turn is the proxy between ASA, ISE PSN and Duo Cloud API.
Cisco ISE part
Besides regular Authentication and Authorization rules Duo Auth Proxy need to be configured as a radius client on Cisco ISE. Cisco ISE acts as:
- Radius Server for Duo Auth Proxy
- Radius Server for ASA VPN
- Proxy for AD authentication
ISE functions in our case study:
- Authentication Server (AD as external identity source)
- Authorization Server for differentiate Users and Groups access privileges
- Accounting Server for log storage and User-to-IP mapping source
In this project User-to-IP mappings are crucial for whole infrastructure because these mappings are used in different segments for identity access. The purpose of identity filtering is described here.
Duo Authentication Proxy
Duo Auth Proxy can be hosted on Linux or Windows Server machine. Duo Authentication proxy is the interface between ISE and ASA, ASA and Cloud API, ISE and Cloud API. You can take a look at the config guides at Duo site https://duo.com/docs/authproxy_reference
Duo Cloud and Active Directory
For the sake of proper authentication, user and mobile devices handling, the Duo Cloud interface is used. There is connection established between Duo Auth Proxy, Duo Cloud API and Active Directory that is used for AD authentication, user and device enrolment with Duo Mobile App.
The solution was integrated with high-availability environment and there is no single point of failure within the VPN infrastructure. For further details of components and their configuration, follow us on Grandmetric LinkedIn site







