Introduction to Wi-Fi Security
Distributing data using wireless medium means that anyone can capture the signal. There is no boundary, like in case of cable communication, which prevents unwanted access. This means we must take other security measures. In this blogpost we will review current algorithms providing Wi-Fi security and we will take a sneak peek into the upcoming – WPA3.
Wired Equivalent Privacy (WEP)
When Wi-Fi was introduced in 1997 there was only one algorithm intended for security, namely WEP – Wired Equivalent Privacy. Its intention was to provide confidentiality equal to the wired transmission.
Security algorithms used in Wi-Fi ensure data integrity and encryption. Integrity provides an information for the user, that the message was not manipulated. Encryption prevents other users from knowing the message content.
In the figure below you can see the data flow in WEP encryption.
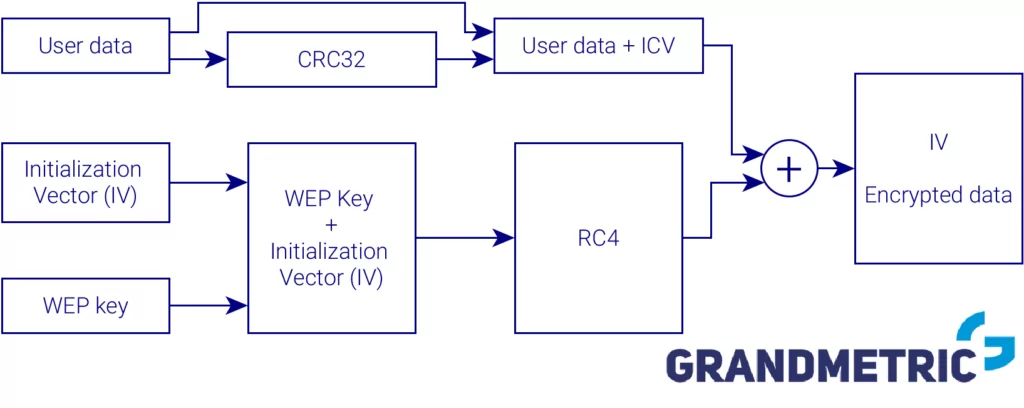
WEP encryption scheme
In WEP, for data integrity 32-bit cyclic redundancy check (CRC32) is used. Integrity Check Vector (ICV) is appended to the user data and forwarded to encryption. This is where first flaw of WEP shows up. CRC32 intention was to detect errors during transmission. This method is not very reliable in message integrity check.
On the other hand, RC4 is used for encryption. This is a stream encryption algorithm, which uses a pair of WEP key (a password) and an Initialization Vector (IV) as a seed. WEP key might either have 40 or 104 bits and IV is always 24 bits long. This makes the seed either 64 or 128 bits long. IV is appended to the encrypted message and its purpose is to avoid using the same seed for encrypting different messages.
As it turns out within few minutes so many packets can be captured, that IV collision reaches a probability of 50%. This makes WEP key easy to be compromised.
It is strongly advised not to use WEP anymore in any circumstances.
Wi-Fi Protected Access (WPA)
IEEE response to the WEP weakness was 802.11i amendment. It introduced a number of security improvements. Since the improvements were urgent and important to introduce, WPA was the answer. It was implemented as part of the 802.11i features and what is important – it was based on the same hardware as WEP, so only firmware upgrade was required to improve the security aspect. Since there were two major flaws in WEP, WPA addressed both of them.
Let’s see the figure below and investigate what are the differences from previous approach.
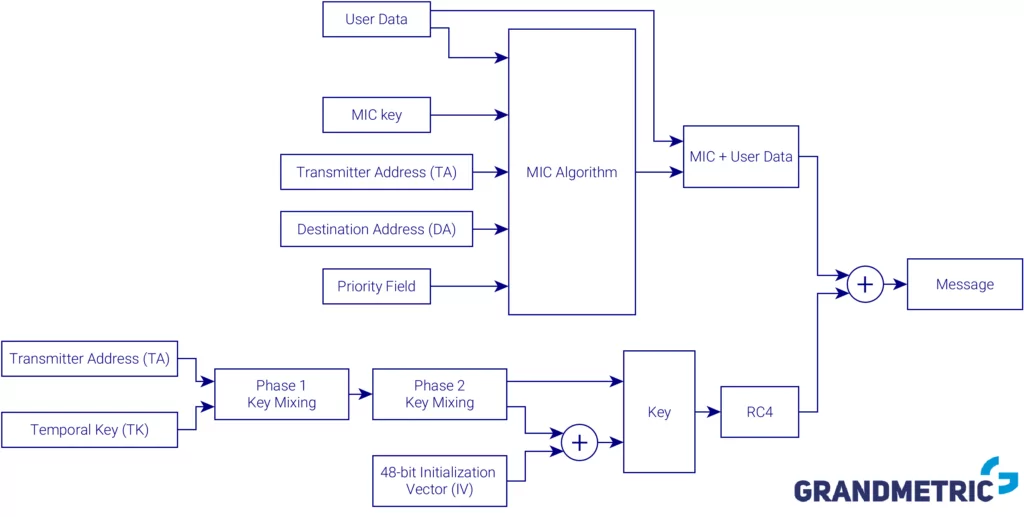
Wi-Fi Security WPA encryption scheme
Encryption was still based on RC4, since it was hardware implementation and couldn’t be updated, but IV was extended to 48 bits. Moreover a master key (so a password you enter in access point and station) is not directly used, but rather it is mixed and encryption key is derived from master key. This makes the main key hard to compromise.
Output message is, as in case of WEP, xor operation of the user data and pseudorandom stream from RC4, but this time the key is much better protected and collision is less likely.
WPA also improved message integrity. It introduced Message Integrity Check (MIC) algorithm, which by design was better suited to this task than CRC32 used in WEP. Algorithm is based not only on the data, but also additional input, such as Transmitter Address, Destination Address, etc. so it is much harder to forge message with correct MIC vector.
It is important to remember, that WPA protects well enough only against those who don’t have a key. If a malicious user is legitimately connected to some network protected with WPA it can capture packets destined for others and decrypt them.
Wi-Fi Protected Access II (WPA2)
WPA2 implements all mandatory features from 802.11i. It provides a significant security improvement over WEP and WPA. The most important architectural change is the data encryption algorithm. In WPA2 the Counter Mode with Cipher block Chaining Message Authentication Code Protocol (CCMP) uses an Advanced Encryption Standard (AES).
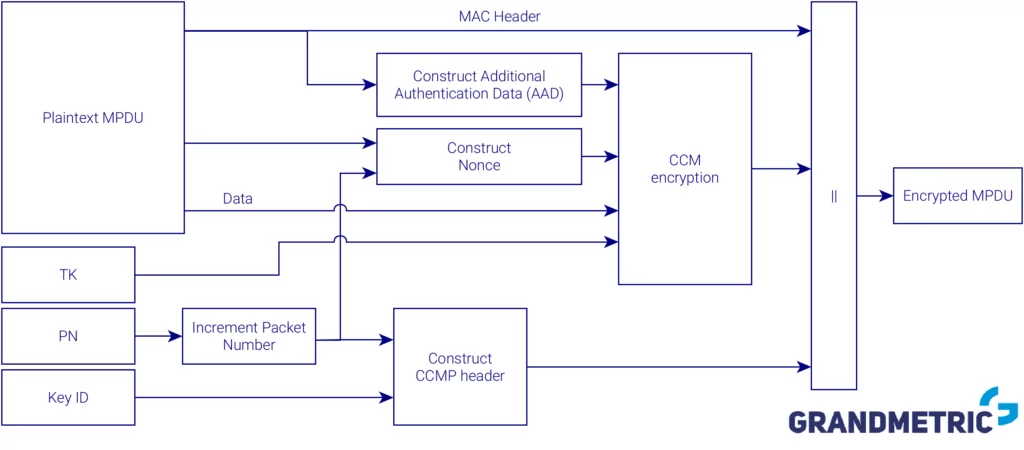
Wi-Fi Security WPA2 encryption scheme
As you can see in the above figure, WPA2 differs from WPA in the way encrypted message and integrity is calculated. In previous systems (WEP and WPA) there was easily distinguished integrity calculation chain and encryption chain. In WPA2 encryption and integrity check are performed within single logical block – CCM. Let’s take a look on the detailed scheme below of this block to know how is integrity and encryption realized in WPA2.
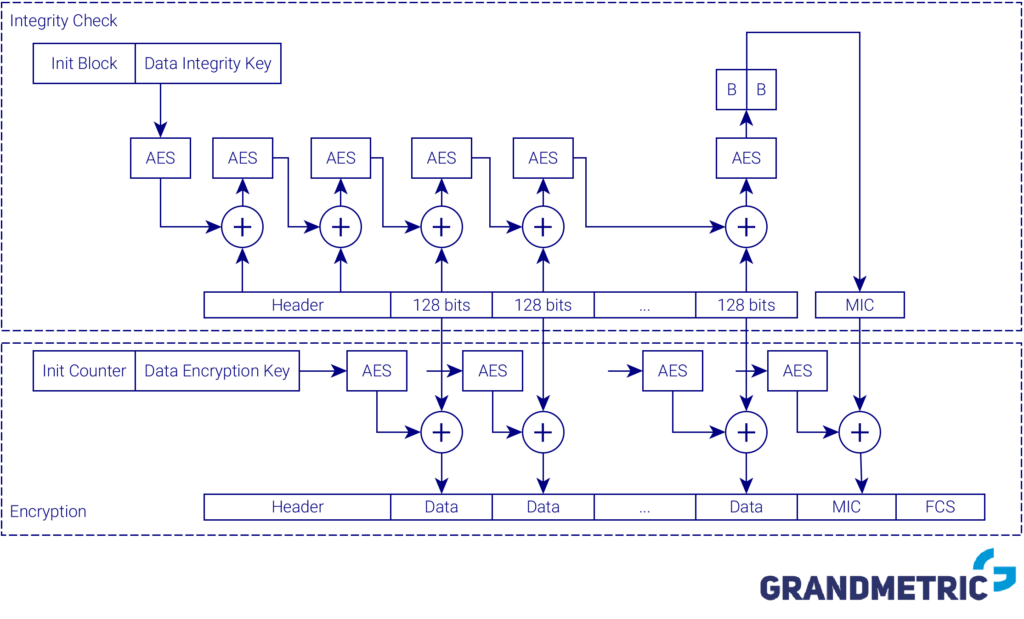
WPA2 encryption and integrity
Both integrity check and encryption are based on Advanced Encryption Standard (AES) algorithm. This is a block-based algorithm, operating on 128 bits chunks. Input message is divided into 128 bits parts and used together with a previous results as an input to the AES algorithm. Whole message, including header is taken into consideration for integrity check, while only payload is encrypted. Header must be transmitted as plain-text in order to enable frame detection and decoding.
WPA3
At the beginning of the year, Wi-Fi Alliance announced that WPA3 will be introduced in the near feature. We learned only about few functionalities, without much details. They kept us waiting for some time, but recently new details were revealed. The aim of WPA3 is to simplify security, enable robust authentication and increase cryptographic strength.
WPA3 comes in two variants WPA3-Personal and WPA3-Enterprise, just like WPA2.
WPA3-Personal
In WPA3-Personal Pre-shared Key (PSK) is no longer in use and Simultaneous Authentication of Equals (SAE) comes in favor. This method is based on key exchange and is resistant to offline dictionary attacks, where previously recorded data can be used to guess password. This mechanism allows to protect the data even if the password is weak, meaning is short or using popular phrases.
WPA3-Enterprise
WPA3 is built upon WPA2, but it provides a number of improvements:
- Authenticated encryption is provided by 256-bit Galois/Counter Mode Protocol (GCMP-256)
- Key derivation uses 384-bit Hashed Message Authentication Mode (HMAC) with Secure Hash Algorithm (SHA)
- Key establishment uses Elliptic Curve Diffie-Hellman (ECDH) exchange and Elliptic Curve Digital Signature Algorithm (ECDSA)
- Frame protection based on 256-bit Broadcast/Multicast Integrity Protocol Galois Message Authentication Code (BIP-GMAC-256)
But that’s not all that comes in this security update. Wi-Fi Alliance also announced Wi-Fi Enhanced Open which is an answer to a problem with open networks eg. at airports, shopping malls or coffee shops. Today you can access these networks freely, often using some captive portal, but the traffic on wireless link is not encrypted. Wi-Fi Enhanced Open will provide unauthenticated data encryption based on Opportunistic Wireless Encryption (OWE).
Summary of Wi-Fi Security
In a table below we summarized what we already learned about WEP, WPA, WPA2 and WPA3 security. The most important conclusion from all previous consideration is that WEP should always be avoided since many flaws were discovered. Devices with old hardware should be updated to use WPA – it uses same RC4 algorithm, but in much safer way. It doesn’t allow such often key collisions and introduces temporal keys. On the other hand, if a device provides hardware support for WPA2 it should be always used. It offers best security in terms of message integrity and encryption. Soon to come WPA3 will improve all aspects of security significantly. Both integrity and encryption will be at even higher level, than we can currently achieve with WPA2.
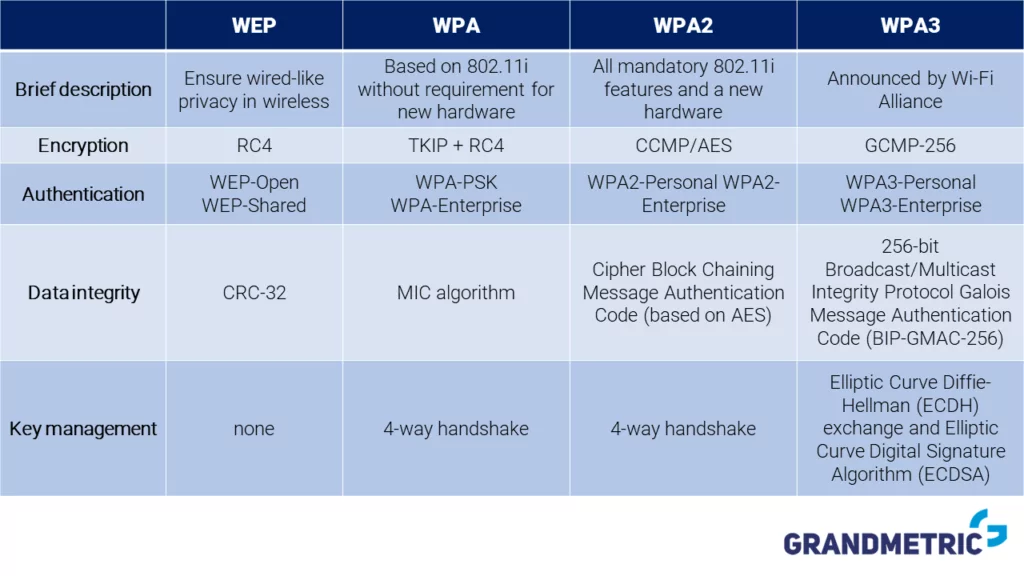
Wi-Fi Security algorithms comparison
Other materials
To see other posts on network and wireless fundamentals see our explained section.
To find out more about Wi-Fi operation and security see our training on Enterprise Wireless Advanced or online video course Wi-Fi Fundamentals.
To subscribe to our mailing list for our online platform where you can learn all this and more (for example all the details on OFDM transmission or Wi-Fi standards evolution) visit GrandmetricWatch.
References
[1] Security | Wi-Fi Alliance
[2] Wi-Fi Alliance Introduces Wi-Fi Certified WPA3 Security | Wi-Fi Alliance
[3] Arif Sari, Mehmet Karay, Comparative Analysis of Wireless Security Protocols: WEP vs WPA










