No matter the attack is original Petya worm or it’s modified version (already called NotPetya), the fact is that it hits biggest brands starting at Ukraine government, Chernobyl power station continuing with Raben, Maersk or St Gobain. So yes, it is disruptive. What we know so far and how we can try to prevent if we have not been hit yet?
- First signs is CHKDSK message
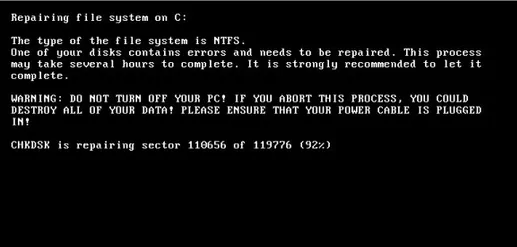
Petya Ransomware Encrypt using CHDSK
If you see this message, switch off your computer immediately! Don’t try to switch on again. Petya needs the restart to finish. Later you could attach your disk to external computer to retrieve your data.
You can also see such variant of this image:
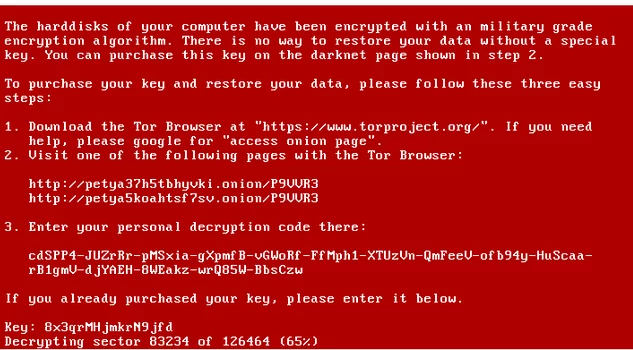
Petya Encrypting Disk – modified screen
If you see this message, switch off your computer immediately as well!
The first two were for already infected OS.
We have read from researchers that to prevent malware from start, you can create a kill switch file that if the worm sees it will stop proceeding (like was with kill switch domain of WannaCry)
Kill switch file: C:\Windows\perfc
Also we have heard from infected administrators that computers with Windows 10 kb4019472 are resistant – not 100% confirmed yet!
And now, something original from Grandmetric.. Because Petya or NotPetya uses PSEX and WMIC tools to spread and these tools uses TCP 445 and TCP 135 accordingly (Windows Domain environment) and additionaly infected hosts still scans the subnet, try to stop the scanning and:
- Step 1: if using firewall inside the network and not using SMB, block 445 and 135 TCp with the ACL or Firewall rule
- Step 2: if not using firewall try to drop 445 and 135 traffic with VLAN ACL:
POD1_SW1(config)#access-list 100 deny tcp any any eq 135
POD1_SW1(config)#access-list 100 deny tcp any any eq 445
POD1_SW1(config)#access-list 101 permit ip any any
POD1_SW1(config)#vlan access-map STOP_PETYA 5
POD1_SW1(config-access-map)# action drop
POD1_SW1(config-access-map)# match ip address 100
POD1_SW1(config)# vlan access-map STOP_PETYA 10
POD1_SW1(config-access-map)# action forward
POD1_SW1(config-access-map)# match ip address 101
POD1_SW1(config)#vlan filter STOP_PETYA_FILTER vlan-list 20
I hope this will have no effect in your example, but it is worth to mention before it’s to late!
Stay connected, we will update this post as soon as we had more info!





Leave a Reply