AWS VPC and data center resources connectivity. Concern.
Lately I was asked about the possibility of building the IPsec tunnel between Amazon VPC and Cisco IOS routers that were located at customer premises (DC). There is quite nice automation tool at Amazon that prepares almost accurate tunnel config for Cisco IOS taking addressing parameters as an input. Anyway the task would not be sophisticated if the main concern would not be related to satisfying different crypto technologies and HSRP simultaneously: static VTI generated by AWS, legacy crypto map that terminates several other S2S tunnels and IPSec HSRP redundancy on the same router. I met few unresolved threads around the networking community that consider SVTI and HSRP IPSec redundancy as unsupported configuration on IOS. However i took the gauntlet and put the config on my lab.
Small piece of tunnel configuration output from AWS automation tool.
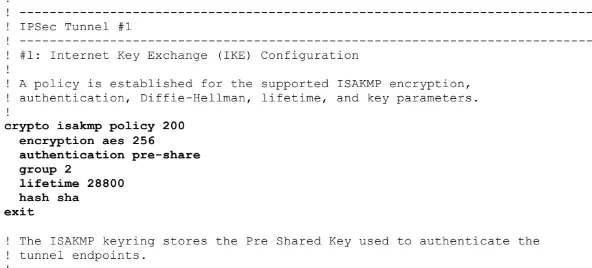
AWS tunnel side
I need to simulate an AWS side. There were no issue with this as the AWS VPC side used purely static VTI interface for connectivity, so I just put the right config that reflected VTI VPN headend (on premise). Here are the most important parts:
Generating crypto keyring to point the peer to proper PSK:
crypto keyring keyring1
local-address 10.253.51.103
pre-shared-key address 10.253.51.203 key KeY$221#$ !--- don't use easy keys :)
Defining crypto policy for phase 1 (ISAKMP):
crypto isakmp policy 200
encr aes 256
authentication pre-share
group 2
lifetime 28800
Making isakmp profile to use with the peer:
crypto isakmp profile isakmp1
keyring keyring1
match identity address 10.253.51.203 255.255.255.255
local-address 10.253.51.103
Time to define security algorithms for phase 2 IPSec:
crypto ipsec security-association replay window-size 128
crypto ipsec transform-set AES esp-aes esp-sha-hmac
mode transport
!
crypto ipsec transform-set set1 esp-aes 256 esp-sha-hmac
crypto ipsec df-bit clear
Bundling transform set perfect forwarding secrecy in one profile:
crypto ipsec profile isakmp1
set transform-set set1
set pfs group2
SVTI configuration:
interface Tunnel1
ip address 10.0.0.2 255.255.255.252
ip virtual-reassembly
ip tcp adjust-mss 1379
tunnel source 10.253.51.103
tunnel destination 10.253.51.203
tunnel mode ipsec ipv4
tunnel protection ipsec profile isakmp1
end
Customer tunnel side
Now is the most important part. Two routers with HSRP IPSec redundancy and legacy crypto map and new SVTI for traffic directed to Amazon VPC.
Router 1 (priority for HSRP)
crypto keyring keyring1
local-address 10.253.51.203
pre-shared-key address 10.253.51.103 key KeY$221#$
crypto isakmp policy 200
encr aes 256
authentication pre-share
group 2
lifetime 28800
!
crypto isakmp key KeY$221#$ address 10.253.51.204
crypto isakmp keepalive 10 10
!
crypto isakmp profile isakmp1
keyring keyring1
match identity address 10.253.51.103 255.255.255.255
local-address 10.253.51.203
!
crypto ipsec security-association replay window-size 128
crypto ipsec transform-set set1 esp-aes 256 esp-sha-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec df-bit clear
!
crypto ipsec profile isakmp1
set transform-set set1
set pfs group2
!
crypto map VPN redundancy replay-interval inbound 1000 outbound 20000
crypto map VPN 1 ipsec-isakmp
set peer 10.253.51.204
set transform-set ESP-3DES-MD5 !--- use AES in production
match address VPN
crypto map VPN redundancy HA-WAN-LAN
HSRP config:
interface FastEthernet0/0
description ---- POD ----
ip address 10.253.51.201 255.255.255.0
duplex auto
speed auto
ipv6 address 2001:41B0:110:A100::1/120
ipv6 nd ra suppress
standby 1 ip 10.253.51.203
standby 1 preempt
standby 1 name HA-WAN-LAN
crypto map VPN redundancy HA-WAN-LAN
SVTI config:
interface Tunnel1
ip address 10.0.0.1 255.255.255.252
ip virtual-reassembly
ip tcp adjust-mss 1379
tunnel source 10.253.51.203
tunnel destination 10.253.51.103
tunnel mode ipsec ipv4
tunnel protection ipsec profile isakmp1
end
Veryfying HSRP state:
FastEthernet0/0 - Group 1
State is Active
4 state changes, last state change 18:23:33
Virtual IP address is 10.253.51.203
Active virtual MAC address is 0000.0c07.ac01
Local virtual MAC address is 0000.0c07.ac01 (v1 default)
Hello time 3 sec, hold time 10 sec
Next hello sent in 2.844 secs
Preemption enabled
Active router is local
Standby router is 10.253.51.202, priority 90 (expires in 7.296 sec)
Priority 100 (default 100)
Group name is "HA-WAN-LAN" (cfgd)
Router 2
crypto pki token default removal timeout 0
!
crypto keyring keyring1
local-address 10.253.51.203
pre-shared-key address 10.253.51.103 key KeY$221#$
!
crypto isakmp policy 200
encr aes 256
authentication pre-share
group 2
lifetime 28800
!
crypto isakmp key cisco address 10.253.51.204
crypto isakmp keepalive 10 10
crypto isakmp profile isakmp1
keyring keyring1
match identity address 10.253.51.103 255.255.255.255
local-address 10.253.51.203
!
crypto ipsec security-association replay window-size 128
crypto ipsec transform-set set1 esp-aes 256 esp-sha-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec df-bit clear
!
crypto ipsec profile isakmp1
set transform-set set1
set pfs group2
!
crypto map VPN redundancy replay-interval inbound 1000 outbound 20000
crypto map VPN 1 ipsec-isakmp
set peer 10.253.51.104
set transform-set ESP-3DES-MD5
match address VPN
crypto map VPN redundancy HA-WAN-LAN
interface FastEthernet0/0.551
description ---- POD ----
encapsulation dot1Q 551
ip address 10.253.51.202 255.255.255.0
ipv6 address 2001:41B0:110:A100::2/120
ipv6 nd prefix 2001:41B0:110:A100::/120 3600 3600
ipv6 nd managed-config-flag
ipv6 dhcp relay destination 2001:41B0:110:B100::5 FastEthernet0/0.550
standby 1 ip 10.253.51.203
standby 1 priority 90
standby 1 name HA-WAN-LAN
crypto map VPN redundancy HA-WAN-LAN
end
!
interface Tunnel1
ip address 10.0.0.1 255.255.255.252
ip virtual-reassembly
ip tcp adjust-mss 1379
tunnel source 10.253.51.203
tunnel destination 10.253.51.103
tunnel mode ipsec ipv4
tunnel protection ipsec profile isakmp1
end
The moment of truth
After configuration landed on IOS we are ready to start traffic verification. I generated the icmp traffic first to simulate communication between legacy VPN sites and customer Data Center LAN.
ICMP from reugular IPSec site to redundant DC VPN hub:
R4#ping 10.10.11.1 so l11
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.11.1, timeout is 2 seconds:
Packet sent with a source address of 10.10.14.1
.!!!!
So far so good. Now lets ping from AWS VPC to DC LAN
R3#ping 10.10.11.1 so l11
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.11.1, timeout is 2 seconds:
Packet sent with a source address of 10.10.10.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 ms
That works! So it is the time to display some outputs to proof the connectivity and encryption goes as supposed to. IKE phase 1 view from legacy site (crypto map):
R4#sh cry isa sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
10.253.51.203 10.253.51.204 QM_IDLE 1003 0 ACTIVE
IPSec SAs view from legacy site (crypto map). Traffic is bidirectional and encrypted:
R4#sh cry ipse sa
interface: FastEthernet0/0
Crypto map tag: VPN, local addr 10.253.51.204
protected vrf: (none)
local ident (addr/mask/prot/port): (10.10.14.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.10.11.0/255.255.255.0/0/0)
current_peer 10.253.51.203 port 500
PERMIT, flags={origin_is_acl,ipsec_sa_request_sent}
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
Output of show crypto isakmp sa on active HSRP router R1. As seen the phase 1 negotiated correctly:
R1#sh cry isa sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
10.253.51.203 10.253.51.204 QM_IDLE 1005 0 ACTIVE !--- Legacy Phase1
10.253.51.203 10.253.51.103 QM_IDLE 1006 0 ACTIVE !--- AWS SVTI Phase1
Output from crypto ipsec sa. The VTI tunnel is working and traffic to AWS is encrypted:
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 10.253.51.203
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 10.253.51.103 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 15, #pkts encrypt: 15, #pkts digest: 15
#pkts decaps: 15, #pkts decrypt: 15, #pkts verify: 15
Also crypto map does its job
interface: FastEthernet0/0
Crypto map tag: VPN, local addr 10.253.51.203
protected vrf: (none)
local ident (addr/mask/prot/port): (10.10.11.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.10.14.0/255.255.255.0/0/0)
current_peer 10.253.51.204 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
In conclusion, my test shows that the Static VTI sourced from HSRP address and legacy Crypto Map (also sourced from the HSRP IP address) with IPSec redundancy can coexist on the same router preserving current corporate VPN tunnels while building Amazon Web Services VPC tunnel connection simultaneously.
Update: Works in production too. Confirmed by the customer :)
Testbed used for this scenario: Cisco ISR routers with IOS Version 12.4(15)T17




Leave a Reply